The Process: Independent Audit and Continuous Monitoring Services
- lexi598
- Oct 23, 2022
- 2 min read
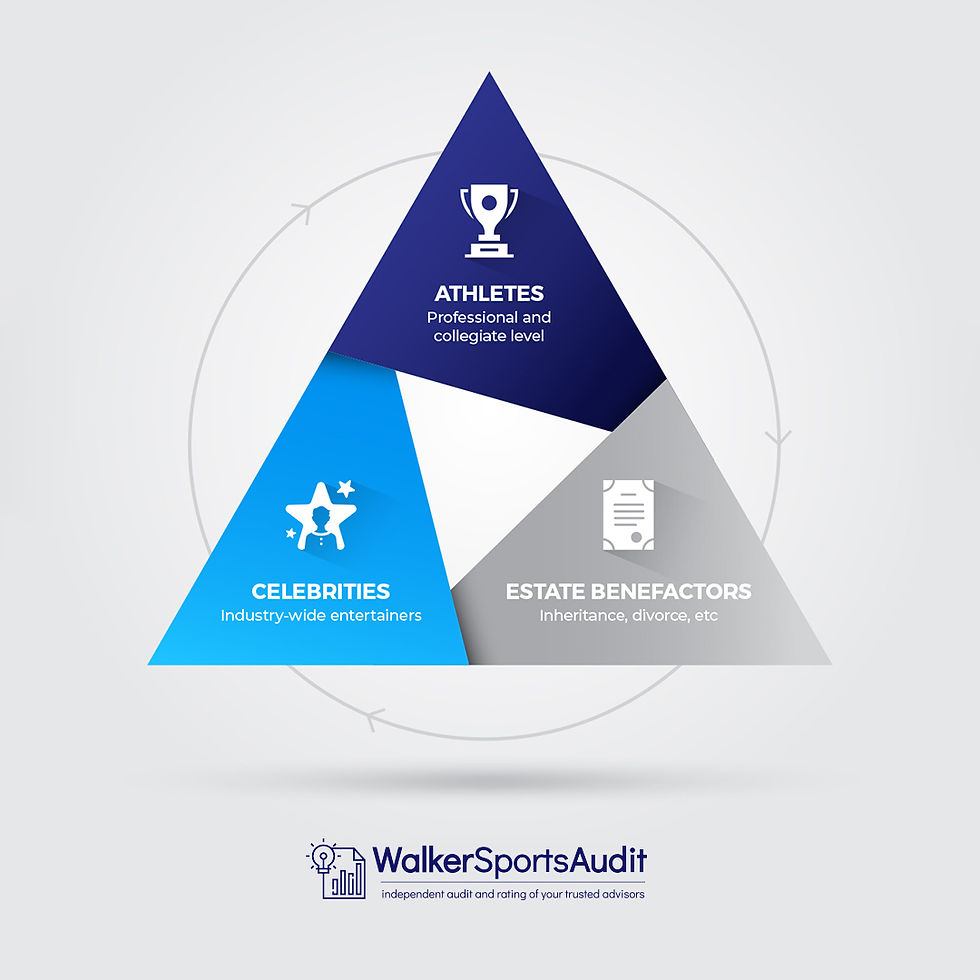
Who We Serve Although we will initially be addressing athletes and celebrities [who fill the news every day with horror stories of how they were ruined by embezzlement from their most trusted advisors], we feel our independent audit and continuous monitoring services will also prove valuable to clients who have considerable estates with little limited personal business acumen or experience. Estates acquired through inheritance or divorce are particularly at risk from unscrupulous or indifferent fiduciary oversight.
What We Do
Gather Financial Documents Review the systems put in place to transmit all of a client’s financial information.
Look at Record-Keeping Look into the client’s record-keeping policies and check to ensure records are being stored properly.
Review the Accounting System Identify and review each element of the client's accounting system, including individual T-accounts (debits and credits), journal entries, the general ledger, and current financial statements.
Review the Internal Control Policies Check into the client's internal controls policies to gauge the level of protection they provide from theft and fraud.
Compare Internal and External Records Compare internal records of cash holdings, investments, commitments, income, and expenses against external records.
Spending Analysis A WSA audit will also help identify spending habits within your finances.
Look at Tax Records Analyze the client's internal tax records and official tax returns.
Uncover & Recover Most successful athletes have reliable and trusted people watching their money, but who is watching them? At one point or another, even the most astute and careful individual might require our independent forensic audit in order to uncover any financial malfeasance or loss.
All of our recovery services are provided on a contingency fee basis. This fee arrangement ensures that our investigative team will not only unearth any breach of trust or misuse of resources but, more importantly, be proactive in the recovery of losses exposed.



![Glassdoor Chief People Officer on Working with Black Progress Executive Staffing [BPX]](https://static.wixstatic.com/media/9694a6_f1ee2a267aca4b77bf862bb454f5d5b4~mv2.gif/v1/fill/w_980,h_737,al_c,usm_0.66_1.00_0.01,pstr/9694a6_f1ee2a267aca4b77bf862bb454f5d5b4~mv2.gif)
Comments